The concept of “Zero Trust” was first coined by University of Stirling doctoral candidate, Stephen Paul Marsh, in 1994. It was 16 years later that Forrester Research analyst, John Kindervag, used the term “Zero Trust Model” to describe a stricter approach to cybersecurity and access controls within corporations.
Since then, achieving Zero Trust has become the holy grail for tech giants like Microsoft, Google and Amazon. It’s also the goal for most IT specialists tasked with securing high risk, or highly regulated organisations against today’s ever-evolving threat landscape.
Of course, that same evolving landscape means the goalposts for Zero Trust are continually shifting, which begs the question: How close are we, really, to achieving true Zero Trust?
To answer that, let’s take a step back and explore what Zero Trust is in the first place, and why it’s become the benchmark for modern security.
What is Zero Trust?
According to Microsoft, “Zero Trust is a proactive, integrated approach to security across all layers of the digital estate that explicitly and continuously verifies every transaction, asserts least privilege, and relies on intelligence, advanced detection, and real-time response to threats.”
Simply put: “Never trust, always verify.”
Because Zero Trust does away with the traditional security perimeter (inside which devices would previously have been assumed trustworthy), it’s also sometimes referred to as perimeterless security.
Why is Zero Trust necessary?
Today’s organisations are no longer confined to neat office blocks with predictable and easy-to-secure connectivity. Instead, modern employees are connecting from locations all over the globe, using diverse cloud services and infrastructure, numerous remote and mobile environments, and a constantly changing range of IoT devices.
In this complex web of technology, it becomes nearly impossible to define and maintain a trusted security perimeter. The only real option is to turn to a Zero Trust approach, where no device (inside or outside the organisation’s digital estate) is ever assumed safe before its identity and health has been verified.
“Security decision-makers (SDMs) say developing a Zero Trust strategy is their #1 security priority, with 96% stating that it’s critical to their organization’s success.”
Microsoft Zero Trust Adoption Report
Side benefits of Zero Trust
“Zero Trust strategy is compelling because it provides increased agility, speed of detecting threats, and improved ability to manage Internet of Things (IoT) and Operational Technology (OT) security.”
Microsoft Zero Trust Adoption Report
Zero Trust is (obviously) primarily about locking threats out. But did you know, Zero Trust security protocols also make it easier to safely open your organisation up for new opportunities?
We’re not just talking about enabling remote work (although the user experience for employees using zero trust security controls like single sign-on is undeniably better). We’re talking about the ability to grant secure and targeted access to very specific content to anyone, anywhere.
That literally opens up worlds of collaborative opportunities with external players that would previously have been considered insupportable security risks. The potential is endless.
The guiding principles of Zero Trust
Transitioning from a traditional security perimeter to a Zero Trust strategy isn’t a simple task. It’s something a lot of organisations are currently grappling with, having been pushed into a remote/hybrid work model by the pandemic.
“81% of enterprise organizations have begun the move toward a hybrid workplace, with 31% fully there. However, 94% have concerns about transitioning, chiefly, employee misuse, increased IT workloads, and cyberattacks.”
Microsoft Zero Trust Adoption Report
These are the guiding principles of Zero Trust that they’ll need to aim for.
- Verify explicitly – make informed security decisions using all available data points, including: identity, location, device health, resource, data classification and anomalies.
- Use least privilege access – limit access to just-in-time (JIT) and just-enough-access (JEA) with risk-based adaptive policies.
- Assume breach – limit potential “blast radius” with micro-segmentation, end-to-end encryption, continuous monitoring and automatic threat detection and response.
Are we there yet?
There’s a common misconception that Zero Trust is a destination – and an achievable one at that. In reality, the constant evolution of threats and technology make it unlikely that anyone will ever truly achieve 100% Zero Trust.
It’s far more accurate to think of Zero Trust as a journey. One that each organisation begins at a different point, with different threats, priorities, and opportunities along the way.
Not sure where you fall in terms of Zero Trust maturity? Check out Microsoft’s maturity model.
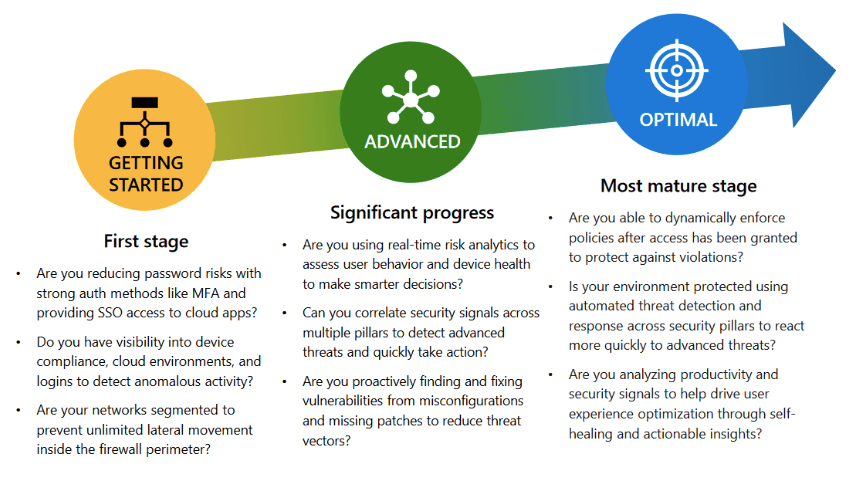
At the end of the day, there is no “one-size-fits-all” solution or single path to achieving Zero Trust. The secret lies in taking the time to step back, analyse your own requirements and challenges, and define a long-term security strategy for your specific environment.
Armed with this strategic knowledge, it’s possible to plan a security roadmap that goes far beyond the “quick fix” to deliver tangible value at every turn. After all, if you’re never truly going to reach your destination, you need to make sure the journey itself is worthwhile.
Get maximum impact with every step you take towards Zero Trust. Book your Microsoft 365 Security Assessment and Roadmap session today!